Online age verification: balancing privacy and the protection of minors
22 September 2022
The CNIL has analysed the main types of age verification systems in order to clarify its position on age verification on the Internet, particularly on pornographic sites for which such verification is mandatory. It specifies how such publishers could fulfil their legal obligations. However, CNIL finds that such current systems are circumventable and intrusive, and calls for the implementation of more privacy-friendly models.

Online age verification: a complex issue with significant privacy risks
Verifying the age of an Internet user is hampered by the difficulty for the various technical stakeholders on the Internet to really know who is the person behind the computer or smartphone. This need to identify Internet users is, in fact, an issue for privacy and personal data protection, since knowledge of an individual's identity can then be linked to their online activity. Yet, this contains particularly sensitive, private information.
In order to visit certain sites or for certain online activities, it is by nature necessary to identify oneself (e.g., to buy a good on an e-commerce site). Age verification, when necessary, takes place in a context where the site publisher already knows certain elements of the identity or personal data of the Internet user (including banking details). On the other hand, where access to the site or an online service does not necessarily require identification, age verification is likely to alter the protection of the Internet user's privacy, by preventing them from visiting the site if they do not provide the publisher with information on their identity.
Informing, raising awareness, and encouraging user control of the systems
Generally speaking, the CNIL recalls the importance of informing and raising awareness among children, parents, legal guardians and staff in the educational community and in youth supervision about good cyber practices, given the growing importance of digital tools in the lives of citizens.
In this respect, as part of its work on the digital rights of minors, the CNIL published general recommendations in August 2021 in which it recalls the requirements it has set to "verify the age of the child and parental consent, while respecting the child's privacy", particularly to comply with the obligations of the GDPR and the Act on minors' access to social networks. Recommendation No. 7, in particular, calls for age verification systems to be structured around six pillars: minimisation, proportionality, robustness, simplicity, standardisation, and third-party intervention.
Finally, the CNIL tends to favour the use of systems under the control of users rather than centralised or imposed solutions: from this point of view, the logic of parental control, leading to a sense of responsibility on the part of the household to limit access to sensitive content, seems to be the most respectful of individuals' rights. However, there is a limit to this logic: the law provides that in certain cases, the publishers of sites (e.g., pornographic sites) are responsible for age verification obligations.
Increasing legal obligations for online age verification
French law and some European regulations impose age requirements on the provision of certain services or goods, requiring the sites in question to verify the age of the customer: purchase of alcohol, online gambling and betting, certain banking services, etc. This requirement generally applies both in the physical world and for online access. Website publishers have therefore implemented age verification systems; such systems are generally considered less intrusive because the legal framework already imposes a relatively robust proof of identity, especially since the transaction will result in an online payment.
In addition, some services contractually impose age requirements (e.g., access to application settings for children).
With a view to better protecting young people online, the Commission anticipates an increase in age verification requirements for certain services. More broadly, the increasing digitisation of public and private procedures increases the importance of providing everyone with the ability to issue only proof of a single attribute (proof of majority, proof of residence, proof of diploma, etc.) without revealing the other elements that constitute an identity. The Commission calls for vigilance so as not to disproportionately increase the requirements for online age verification, leading to a reduction in the number of sites that can be freely visited.
For pornographic sites, age verification provided for by law and reaffirmed in 2020
In the specific case of sites disseminating pornographic content, the Law of 30 July 2020 aimed at protecting victims of domestic violence reaffirmed the obligations regarding age verification, which are codified in Article 227-24 of the French Criminal Code. The act of disseminating a "message of a pornographic nature" likely to be seen by minors is thus punishable by law, with the law specifying that age verification cannot result from a simple declaration by the Internet user that they are at least 18 years old.
The Chair of the Audiovisual and Digital Communication Regulatory Authority (Arcom), within the framework of the powers entrusted to it, ordered several pornographic sites, in December 2021, to implement an effective age verification of Internet users. As these orders were not followed up on, in March 2022, the Arcom Chair asked the president of the Paris judicial court, pursuant to the Law of 30 July 2020 to block sites allowing minors to access pornographic content, in violation of Article 227-24 of the French Criminal Code.
On 3 June 2021, the CNIL issued an opinion on the draft decree specifying, for the application of the Law of 30 July 2020, the obligations of sites disseminating pornographic content. On this occasion, it specified some main principles in order to reconcile protection of privacy and youth protection, through the implementation of online age verification systems for pornographic sites:
- no direct collection of identity documentation by the publisher of the pornographic site;
- no age estimates based on the user's web browsing history;
- no processing of biometric data for the purpose of uniquely identifying or authenticating a natural person (e.g., by comparing, via facial recognition technology, a photograph on an identity document with a self-portrait or selfie).
The CNIL also recommends, more generally, the use of a trusted independent third party to prevent the direct transmission of identifying data about the user to the site or application offering pornographic content. With its recommendations, the CNIL is pursuing the dual objective of preventing minors from viewing content that is inappropriate for their age, while minimising the data collected on Internet users by the publishers of pornographic sites.
In this context, the CNIL issues several recommendations and warnings.
CNIL's recommendations and warnings about online age verification
The need to manage, in the short term, age verification solutions by involving a trusted third party
Age verification criteria that raise important issues
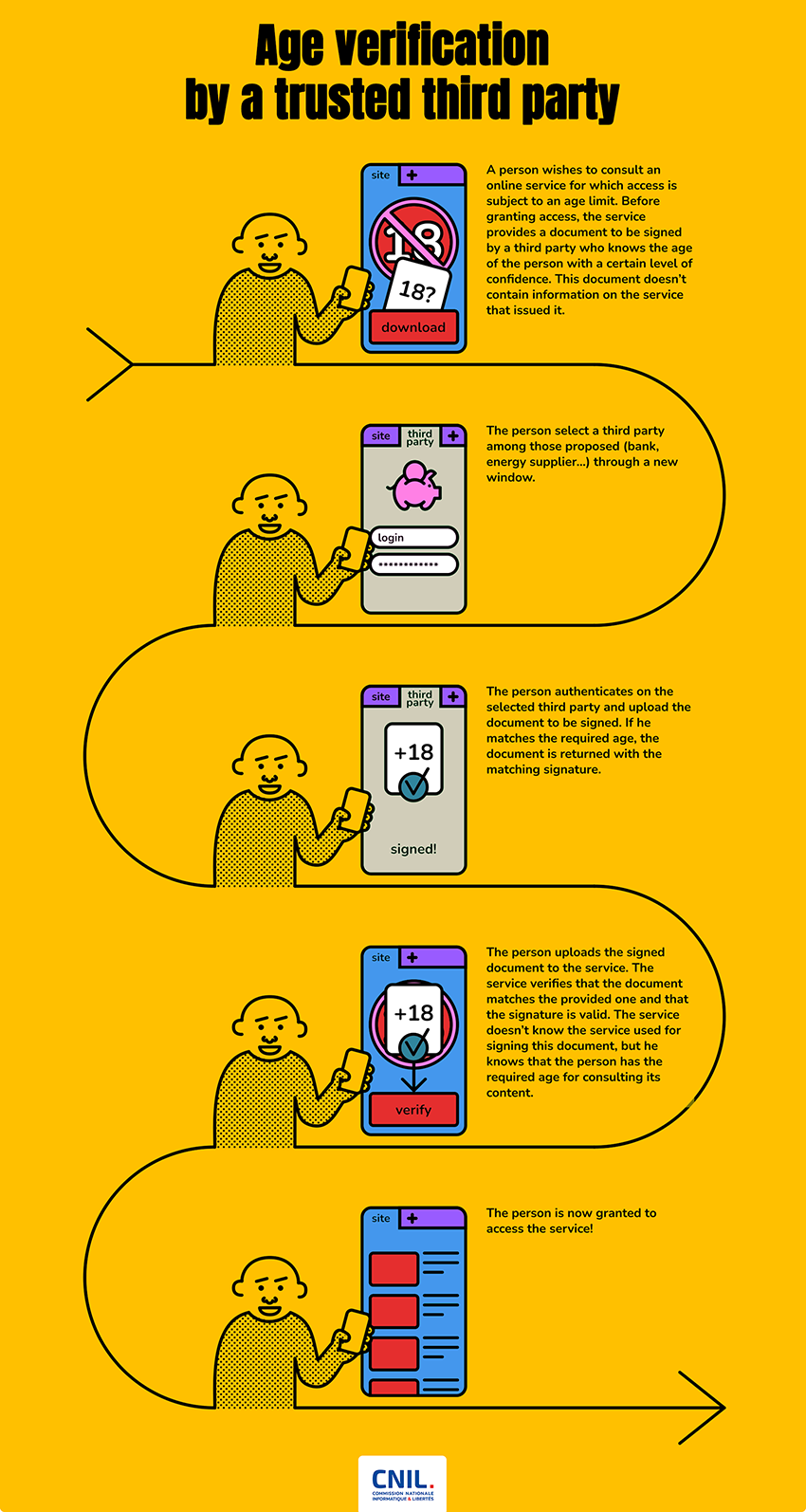
In the context of the use of a trusted third party, recommended by the CNIL in its opinion of 3 June 2021, the age verification, in practice, is divided into two separate operations:
- On the one hand, the issuance of proof of age: the implementation of a system to validate the information on the age of the individual, by issuing a proof of age featuring a confidence level. This proof can be issued by different entities that know the Internet user, whether they are providers specialised in digital identity provision or an organisation that knows the Internet user in another context (a merchant, a bank, an administration, etc.). Different solutions are analysed in this paper.
- On the other hand, the transmission of this certified proof of age to the site visited, so that the latter can give access to the requested content or not (note that, as indicated in the PEReN note, a third step consists in analysing the proof of age presented and giving access to the requested content, or not).
These two aspects involve important data protection and privacy issues, particularly to preserve the possibility of using the Internet without revealing one's identity or directly identifying data. Entrusting such functions to different stakeholders makes possible a three-fold protection of privacy:
- the entity providing the proof of age knows the identity of the Internet user but does not know which site the latter is visiting;
- the person who sends the proof of age to the site may know the site or service that the user is visiting but does not know their identity (in the "ideal" solution described below, the proof of age passes through the user, which allows for compartmentalisation between the stakeholders);
- the site or service knows the age of the user (or just their majority) and knows that they are visiting that site, but does not know their identity or, in some cases, the age verification service used.
An independent third-party auditor to best protect individuals' data
In order to preserve the trust between all of the stakeholders and a high level of data protection, the CNIL therefore recommends that sites subject to age verification requirements should not carry out age verification operations themselves, but should rely on third-party solutions whose validity has been independently verified.
For the function of transmitting a validated proof of age to a site, the CNIL recommends the use of an independent third-party verifier, whose use is under the control of the individual.
Such an independent third party would be responsible, on the one hand, for selecting one or more solutions that would make it possible to issue a valid proof of age (see below) and, on the other hand, for guaranteeing to the site visited that the user is of the required age to access the requested content by means of cryptographic signatures that make it possible to verify the authenticity of the information and its source. The demo developed by the CNIL with Olivier Blazy, professor at the École Polytechnique and the Central government digital regulation expertise centre (Pôle d'expertise de la régulation numérique de l'État - PEReN), provides one possible implementation modality (see end of this page). The mechanisms implemented in this proof of concept prevent:
- the third party transmitting the proof of age from being aware of the site visited;
- the site visited from knowing the provider of the proof of age.
This trusted third party could, more generally and beyond age verification alone, take the form of an "attribute management" service, which would offer each user the possibility of disclosing information from well-identified data providers (e.g., an electricity company to certify an address, an identity service to certify an age) and selected by the user themself.
The work of the European Commission is moving in this direction, as shown in the Communication "the new European strategy for a better internet for kids" (PDF), particularly in the context of the proposal for a European Digital Identity.
A necessary assessment of third-party proof-of-age providers
In addition, there also seems to be a general need for third-party evaluation of proof-of-age providers, especially when they implement an approach based on an automatic or statistical analysis.
To this end, and in view of the sensitivity of the data collected and the intrusive nature of age verification systems and, more broadly, of the processing of identity-related information, the creation of a specific label or certification for such third-party stakeholders for the entire proof-of-age management cycle (from its issue to its use) could make it possible to ensure the compliance of the systems with the GDPR (compliance with the principles of minimisation, security of the data collected, and purpose).
The CNIL believes that this certification procedure could be inspired by, and simplify, the existing framework for remote identity verification providers (PVID), which requires ANSSI qualification on the basis of precise, auditable standards.
This certification should be clearly communicated so that each user can easily attest to the quality and reliability of the service offered. When implemented, a non-certified age verification system should not be deployed on a permanent basis, particularly to avoid the use of "fake" age verification services seeking to fraudulently capture personal data (in order to resell it, re-use it for other purposes not authorised by the user, etc.).
An inevitably imperfect verification
With regard to the devices currently available on the market, the CNIL would first like to stress that the effectiveness of age verification tools depends on the operating rules of the Internet, which is designed as an open network, freely accessible to site users and publishers. While this finding should not prevent the pursuit of the legitimate objectives of protecting minors, care should also be taken to preserve the many benefits linked to this open model (innovation, freedom of expression, user autonomy, etc.). The move towards a closed digital world, where individuals are encouraged to register mainly in authenticated universes (via the creation of user accounts) to avoid a multiplication of identity or identity attribute verifications (age, address, diplomas, etc.) presents significant risks for the rights and freedoms of individuals, which need to be taken into account.
At present, all the solutions proposed can easily be circumvented. Indeed, the use of a simple VPN locating the Internet user in a country that does not require an age verification of this order can allow a minor to bypass an age verification system applied in France, or to bypass the blocking of a website that does not comply with its legal obligations. Similarly, it is difficult to certify that the person using a proof of age is the one who obtained it.
For example, in the UK, where such measures have long been considered, 23% of minors say they can bypass blocking measures and some pornographic content publishers already offer VPN services.
If the use of VPNs must be subject to a certain vigilance, it should be stressed that such technologies are also one of the essential building blocks of the security of exchanges on the Internet, used by many companies, but also by individuals wishing to protect their browsing from the tracking conducted by public or private stakeholders.
Analysis of existing solutions
The CNIL has analysed several existing solutions for online age verification, checking whether they have the following properties: sufficiently reliable verification, complete coverage of the population and respect for the protection of individuals' data and privacy and their security.
The CNIL finds that there is currently no solution that satisfactorily meets these three requirements. It therefore calls on public authorities and stakeholders to develop new solutions, following the recommendations described above. The CNIL deems it urgent that more effective, reliable and privacy-friendly devices be proposed and regulated as soon as possible. Article 3 of Decree No. 2021-1306 of 7 October 2021 entrusts Arcom with the task of drawing up guidelines detailing the reliability of the technical procedures that websites must implement to prevent access by minors.
More generally, benchmarks and labelling or certification systems are likely to enable and facilitate the rapid development of trust solutions.
However, there are already mechanisms in place to improve the level of protection of minors, especially the youngest. Several solutions are detailed below, in decreasing order of maturity from the CNIL's point of view. Pending the implementation of a suitable framework, and for a transitional period only, the CNIL believes that some of these solutions may make it possible to strengthen the protection of minors, provided that care is taken with regard to their implementation and in particular to the additional risks generated by their use.
-
Age verification through payment card validation
Age verification through payment card has the advantage of relying only on already deployed and proven infrastructures. Thus, even if this type of verification is circumventable (since minors may be in possession of payment cards enabling them to make purchases on the Internet) and not accessible to all (since adults may not have such a card, notably because of social discrimination, given the differences in access to a credit card according to income). This solution is already being implemented by a number of stakeholders. The system is based on verifying the validity of the card and not on a payment (although some verifiers process a micro-payment, which is immediately cancelled), which can also be used for access verification on free sites.
Although payment systems are not designed to verify attributes, particularly the age of the cardholder (or their majority), they can help to prevent minors from accessing sites or services not intended for them, subject to certain conditions. Such a system makes it possible, in particular, to protect the youngest children (up to about the age of 10-11 years), who cannot have a bank card for online payments and for whom the likelihood of using a third party's card is the lowest.
On the one hand, such an age verification system should, in principle, not be implemented directly by the data controller (i.e., the website visited) but by an independent third party. On the other hand, the systems put in place should ensure the security of the verification, in order to prevent the risks of phishing that will be associated with it. It is therefore important to ensure that payment information is entered on trusted sites. If this solution is chosen, it would be advisable for website publishers and solution providers to launch a parallel campaign to raise awareness of the risks of phishing, particularly taking into account this new practice. Free access should remain free: there should be no cost to the user to use the system.
-
Age verification through an estimate based on facial analysis
Some age estimate procedures are based on facial analysis, but are not intended to identify the individual. In order to prevent young people accessing an adults-only service, this type of estimate is often sufficient, as the margin of error is concentrated on minors and minors close to 18 years of age or young adults and adults. However, for those who may dispute the estimate, it is necessary to have an alternative verification method.
The use of such systems, because of their intrusive aspect (access to the camera on the user's device during an initial enrolment with a third party, or a one-off verification by the same third party, which may be the source of blackmail via the webcam when accessing a pornographic site is requested), as well as because of the margin of error inherent in any statistical evaluation, should imperatively be conditional upon compliance with operating, reliability and performance standards. Such requirements should be independently verified.
This type of method must also be implemented by a trusted third party respecting precise specifications, particularly concerning access to pornographic sites. Thus, an age estimate performed locally on the user's terminal should be preferred in order to minimise the risk of data leakage. In the absence of such a framework, this method should not be deployed.
Requirements: To limit the risk of video capture and possible blackmail, age verification solutions using facial analysis should be certified and deployed by a trusted third party in accordance with precise specifications.
-
The offline verification system
The offline verification method that appears to be the most successful is the marketing of "scratch cards" to adult individuals only, allowing them to retrieve a login identifier and password that would give them access to age-restricted content. Such cards would be offered in certain sales outlets, such as supermarkets or tobacco shops, whose staff already carry out age verifications in connection with the sale of alcohol, cigarettes and gambling.
However, this modality cannot be deployed for the sole purpose of consulting pornographic sites, as it could be stigmatising for the individual concerned. All age-restricted activities should be associated with it, and this model should be promoted by a diverse community of publishers (purchases of regulated products, pornography, etc.). The limitations of such a system would be the same as for the purchase of cigarettes or alcohol, namely fraud by reselling cards on a parallel market.
Requirements: This modality requires specific governance, with an authority issuing the cards and managing the authentication systems.
-
Age verification through an analysis of identity documentation
Age verification may be carried out by a third-party actor collecting and analysing an identity document provided by the user. Such a system is easily circumvented by using another person's identity document if only a copy of the document is needed (possibility of using a document of another individual who is an adult, even within the household). This system is therefore both unreliable and not very respectful of personal data, as it requires the collection and processing of official proof of identity in order to function.
Some systems verify the identity of the individual by comparing the photograph in the identity document provided with a "live detection test", i.e., the capture of a photograph or video taken by the user at the time of the age verification request, in order to verify that the user is the individual they claim to be, and to counter a possible circumvention of the system. This process is much more reliable and is also used for identity verification according to the ANSSI's PVID standard.
However, as soon as it leads to the processing of biometric data, its use should be particularly regulated and must, in principle, be provided for by a specific legal standard or be based on the free consent of the individuals. If it is to be used, it should be in the context of a certified (or labelled) identity manager, under the conditions set out below.
Requirements: As with the PVID standard, it is necessary to set up a certification (or labelling) body that will make it possible to verify that the necessary guarantees for the collection and analysis of identity documentation are in place.
-
The use of central government-provided tools to verify identity and age
The use of public databases or an authentication system such as FranceConnect could theoretically make it possible to prove one's age for access to certain sites or online services. However, FranceConnect was not designed with this in mind, but with a view to simplifying administrative procedures: its very operation is based on the logging of uses on central government servers. This method does not therefore appear satisfactory, since it would lead the central government to have a list of connections of a purely private nature. Moreover, with regard to the consultation of pornographic sites, the use of such systems would lead to a risk of associating an official identity with private information and an assumed sexual orientation.
On the other hand, as explained above, the connection of an attribute management service operated by a trusted third party to central government identity systems could be considered.
Requirements: it is necessary to deploy trusted third parties connecting attribute management services to central government identity systems.
-
Inferential age verification systems
There are three main variations of this type of analysis: the first appears difficult to reconcile with data protection, while the second raises questions of reliability. The third, which also raises important questions, can moreover only be used by a small number of services that already collect a lot of browsing data.
- Importing the individual's Internet browsing history: this method seems too intrusive for the simple purpose of age verification.
- The analysis of the "maturity" by questionnaire: this method seems to be able to avoid the transfer of personal data. However, this method appears to be relatively reliable and the possibility of circumvention is high (online sharing of responses), as are the biases that could be associated with it. For example, a part of the population could be discriminated against on the basis of their skills (reading, comprehension), their level of language proficiency, their cultural references, etc. This method should therefore be avoided.
- Analysis of browsing on the site publisher's own services (particularly the major digital platforms). The reuse of data for age inference (or deduction) models appears to be possible, subject to the following points:
- This method should not, in principle, lead to an automated decision, but to an initial assessment which may, if there is a suspicion of non-compliance with the age requirement, lead to an exchange with the user;
- no additional data should be collected for the sole purpose of building the model (only data already collected is used);
- data produced on the platform's services must be distinguished from data collected by tracking the user's browsing on other sites (e.g., by being authenticated on the platform, by installing a mechanism for tracking access to certain web pages, etc.);
- the inference system should be evaluated by an independent third party, in order to limit its risks.
CNIL's exploratory work on a privacy-friendly age verification system
Whatever technique is used to verify age, it is necessary to ensure its reliability, the confidentiality of the information, and to minimise the data exchanged.
To this end, the CNIL's Digital Innovation Laboratory (LINC), in partnership with Olivier Blazy and PEReN, has demonstrated the feasibility of a system based on a secure protocol using "zero-knowledge proofs": Demo of the privacy-friendly age verification mechanism.
This protocol is based on a process used in cryptology that allows identified individuals to prove a situation without having to reveal any further information.
This demo shows that it is possible, through a third-party system, to guarantee the protection of the individual's identity and the principle of data minimisation, while maintaining a high level of assurance on the accuracy of the data transmitted. However, it assumes that the third parties used are completely independent of the publishers.
Read more
- Recommendation No. 7, in particular, calls for age verification systems to be structured around six pillars
- Demonstration of a privacy-preserving age verification process - LINC
- LINCnil / SigGroup
- Digital rights of children
- [FR] Vérification de l’âge en ligne : trouver l’équilibre entre protection des mineurs et respect de la vie privée